
For every online threat, there’s a shield to protect your business and your customers – here's everything you need to know, including how Vodafone Business can help.
Despite waves of high-profile cybersecurity attacks dominating the headlines, it’s tempting for small businesses to think that cybersecurity is only a problem for multinational household names and other big enterprises. But that couldn’t be further from the truth – in a recent survey by the Federation of Small Businesses, 41% of small firms surveyed had suffered from a cyber-attack.
Even more alarming, 23% of those surveyed said that the average cyberattack – which causes damage worth around £3,320 – would be enough to wipe out their business. Even if a cyberattack doesn’t force your firm to shut down, the reputational damage – especially if cybercriminals gain access to some or all of your customers’ data – can be extremely serious.
Although cybersecurity can seem like an intimidatingly complex topic, the types of cybersecurity threats facing small businesses are straightforward to understand and defend against. Here’s what you need to know.
Malware
‘Malware’ is any malicious software, including viruses, that can penetrate your computer or IT systems and inflict damage such as:
- causing a computing device to become unusable or locked;
- stealing, deleting or encrypting data;
- taking control of your computing devices to attack other organisations;
- obtaining credentials which allow access to your organisation’s systems or services that you use.
‘Malware’ includes not only viruses, which can automatically make copies of themselves to infect other computers and devices, but also Trojan Horses which is malware disguised as legitimate software.
Malware can infect your computers or systems through several channels, from hacked websites, online adverts and downloaded files to apps and external storage such as USB drives.
To combat malware:
- Centrally manage your devices, so that they can only run approved apps, services and technologies that you trust.
- Keep all software on your devices up-to-date, especially the latest security patches.
- Prevent access to suspicious websites.
- Ensure incoming files, as well as your computing devices generally, are scanned for malware.
- Regularly make multiple backups of your data.
- Trend Micro’s Worry-Free Service, offered by Vodafone, can help protect your business devices against malware and warn you about potential vulnerabilities such as out-of-date software on your computing devices.
Ransomware
Ransomware is a type of malware that steals private data, such as customer information, or blocks your access to it by encrypting the data or locking you out of your computing devices. The criminals responsible say that the private data will only be returned, or your devices unlocked, if you pay them money as a ransom.
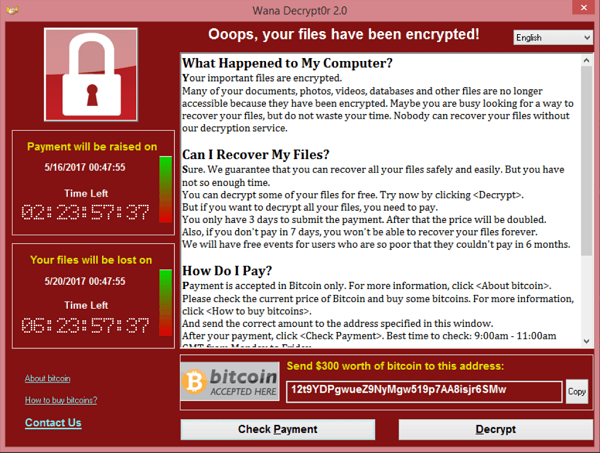
The National Cyber Security Centre advises: “law enforcement do not encourage, endorse, nor condone the payment of ransom demands.” Even if you decide to pay their ransom, there’s no guarantee that the criminals responsible will keep their word. Plus, the ransomware will still be on your systems, increasing the chances that you’ll be targeted again in future.
To combat ransomware, follow the steps mentioned above on how to combat malware in general. Regular, multiple backups of your data is always critically important, but it’s especially useful in recovering from a ransomware attack. If you have a complete and recent backup of all your data, then the threat of ransomware to your business is lessened.
Credential stuffing
If you and your staff reuse the same usernames and passwords to log in to your computers and services, then you’re vulnerable to credential stuffing. This is when cybercriminals fraudulently obtain your login details from one service and attempt to reuse them on others. They will often do so using automated tools, resulting in tell-tale signs that such an attack is underway, from unexpectedly high traffic on a website to repeated login failures over a short period of time.
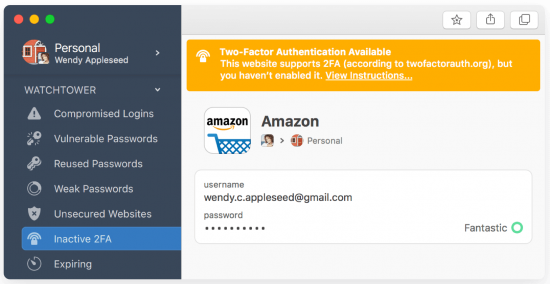
To combat credential stuffing:
- Where available, use multifactor authentication – also known as two factor authentication (MFA or 2FA). This requires two different forms of evidence to prove one’s identity when logging in. The first is your password, while the second is often a code sent through a dedicated MFA app or through email or text massage.
This provides extra security, especially when the password is known by a cybercriminal. - Train your staff to avoid reusing passwords as well as using weak, easily guessed passwords. Password manager services and programs are available, which can not only create unique and complex passwords but help staff use them without having to memorise them.
Distributed Denial of Service (DDOS)
These attacks are typically executed by an army of infected computers which work together to flood a target website with so much traffic that the site goes down. An effective DDoS attack prevents a business from running its day-to-day operations, leading to lost revenue and productivity during the time it takes to sort the problem out.

With DDOS attacks, prevention and preparation is key. When choosing your website hosting provider, ask them about what technical measures and defences they have against DDOS attacks.
Phishing
‘Phishing’ emails are sent by cybercriminals posing as someone else, such as a colleague, supplier, customer or public authority. By posing as someone trustworthy, phishing emails hope to dupe the reader into supplying sensitive information or performing other sensitive tasks for financial gain or identity theft. Phishing emails can also contain malicious links which, when clicked, can lead to other cybersecurity threats such as the unintended installation of malware or ransomware.
To combat phishing, train your staff:
- to spot suspicious emails – tell-tale signs include low-quality graphics, poor spelling and grammar, requests inconsistent with usual company practice as well as language that’s threatening or out of character for the sender;
- so they know what to do when faced with unusual requests and feel comfortable challenging them;
- to challenge the senders of suspect emails and how to confirm their identity.
Plus, security software, such as Lookout Mobile Security and Trend Micro Worry-Free Service which are both available from Vodafone, can help protect your staff from phishing emails and suspicious links.
Data breach
The steps listed above can help lessen your business’ chances of falling prey to a cybersecurity attack. Even so, you still need to prepare in case cybercriminals do successfully gain access to your data or your customer’s data.
Such data breaches need an incident response plan and an incident response team that can implement it. That team needs to be aware of what data your business collects and what your legal obligations are, both to your customers and to the authorities, in the event of a data breach.
For more information on how to prepare an incident response plan and team for your small business, as well as for more detail on cybersecurity defences, read the full report from Vodafone Business and Entrepreneurial Britain.
Stay up-to-date with the very latest news from Vodafone by following us on Twitter and signing up for News Centre website notifications.








